May 25, 2024
The Wisdom of Crowds: How Zero Trust is Sensor Fusion
Exploring zero trust and its relationship to sensor fusion to reduce uncertainty and cyber risk for enterprises
Imperfect sensors for an imperfect world
In an imperfect world where cyber threats are constantly evolving, relying on a single sensor or security control is not enough. Just like no single sensor can capture all the details of the physical world, no single security control can provide comprehensive protection against cyber threats. This is where sensor fusion comes into play. By combining the inputs from multiple sensors, we can overcome the limitations of individual sensors and obtain a more accurate and complete picture of the environment.
In this blog post we explore how Zero Trust is like sensor fusion. And answer questions like:
- how can Zero Trust help to minimize uncertainty and risk?
- how can sensor fusion be seen in NIST's high level Zero Trust architecture?
- how can we harness the Wisdom of Crowds to implement Zero Trust?
Read on to learn more.
Sensor Fusion as a way to reduce risk
 Partial visibility of cyber attacks, and imperfect logging, telemetry and controls is uncertainty in our cybersecurity control architectures.
Partial visibility of cyber attacks, and imperfect logging, telemetry and controls is uncertainty in our cybersecurity control architectures.
We should solve it the same way it is done in other branches of engineering: everything from radar systems to ball tracking in sports, to self-driving cars solve this problem the same way... sensor fusion.
Sensor fusion is a concept and phenomenon from Control Theory engineering that allows us to better model the real world by improving situational awareness and reducing the risk of accidents. It has proven to be effective at reducing uncertainty from imperfect sensors across various domains.
Examples range from monitoring the the temperature in a greenhouse; to flight patterns of aircraft; autonomous vehicles and robotics; to the stability of a nuclear reactor...
- ...or even the security of a digital asset!
What is Sensor Fusion?
Sensor fusion involves integrating data from various sensors to make better-informed decisions. Similarly, in the realm of cybersecurity, zero trust takes a similar approach by combining multiple security controls to reduce uncertainty and minimize cyber risk. Zero trust assumes that no user or device should be trusted by default, and instead, every access request is treated as potentially malicious. This approach allows organizations to continuously evaluate and verify the trustworthiness of users and devices, ensuring that only authorized entities can access sensitive resources.
In cybersecurity, the concept of sensor fusion can be applied to enhance the detection and response capabilities of an organization. By combining the outputs of different security controls, organizations can gain a holistic view of their network and identify potential threats more accurately. For example, if a firewall detects suspicious network traffic, and an intrusion detection system (IDS) detects anomalous behavior within the network, combining these alerts can provide a more comprehensive understanding of the potential threat. This integrated approach enables organizations to respond swiftly and effectively to mitigate risks.
Assume Breach, Assume Noise
Zero Trust can be viewed as a form of sensor fusion in the context of cybersecurity. Instead of assuming security systems are perfect, and risk signals have no uncertainty, we should assume noise.
Instead of relying on a single security control, zero trust can be viewed as combining multiple assumed noisy controls to create a layered defense approach that reduces uncertainty at access time and session time. This both allows security teams to prevent attacks, and better detect and respond to ongoing attacks.
By implementing zero trust principles, organizations can fuse together risk signal sources. This allows you to leverage the strengths and reduce the weaknesses of various disparate, noisy security controls.
Zero Trust is Sensor Fusion
Take the seminal whitepaper on Zero Trust from the National Institute for Standard's in Technology - NIST SP 800-207. In the special publication, NIST introduces the concept of a "Policy Decision Point" and it's subcomponent the "Policy Engine", which makes decisions using a Trust Algorithm based on risk/trust signals.
The second figure in the whitepaper shows high level logical components of how a Zero Trust Architecture with a Policy Decision Point and Enforcement Point (the Security Control) implements zero trust control between a Subject and an Enterprise Resource. It depicts how other systems need to feed in data to the Policy Decision Point in order for it to make decisions about which Subjects to trust and when.

These are risk signals. And in NIST's example, the PDP combines risk signals from eight different enterprise tools (CDM systems, compliance systems, threat intelligence, activity logs, IDAM, SIEM, etc) in order to better understand the risk context to the currently requested session.
The Policy Decision outputted therefore benefits from reduced uncertainty by combining all these signals from all these systems. If the outputted decision is to temporarily trust this subject to this resource for this session, that risk might be considered lower due to the greater degree of certainty from sensor fusion.
This can be viewed on the NIST diagram as follows:

How this helps identify risk
To make it real, let's consider an example of how Zero Trust Sensor Fusion helps identify risk where we couldn't previously:
Let's take an attack scenario where we have a remote attacker who already has a foot hold on an enterprise endpoint... in this case, when the legitimate user is also logged into their device and initiates a session to an Enterprise Resource:
- Our user logins with MFA so our authentication signals show LOW risk,
- Device validation might show LOW risk as it's a fully patched, compliant device,
- User behavior analytics might show MEDIUM risk as there's a slight change in the behavior of this user when the remote attacker is also logged in, but the remote attacker might not have moved the needle far enough for this alone to trigger as high risk
- And finally our EDR agent on the endpoint shows unsusual processes running that depart from other devices like this, or depart from the usual pattern of behavior of this device; but don't flag as malicious - so another MEDIUM risk signal.
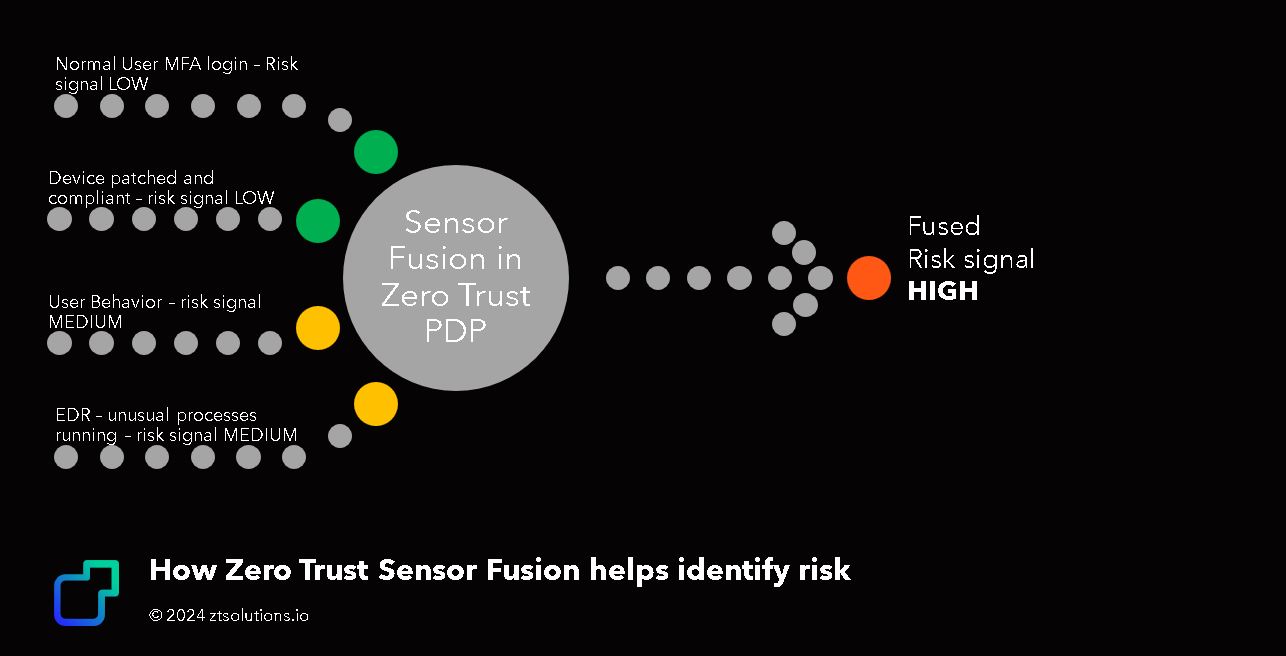
You can also view this as another important reason to implement defense-in-depth. It's a layered approach that ensures that even if one control fails (or has too much noise and not enough signal) or is bypassed, there are other controls in place to detect and prevent potential threats.
Just like sensor fusion enhances the accuracy and reliability of information in the physical world, zero trust enhances the security of digital environments by fusing multiple assumed noisy security controls.
Harness the Wisdom of Crowds (of Security Controls)... Implement Zero Trust
The concept of harnessing the wisdom of crowds can be applied to cybersecurity through the implementation of zero trust.
Instead of relying on a single security control or the expertise of a few individuals, zero trust leverages the collective intelligence of multiple security controls to make informed decisions.
By implementing zero trust, organizations can benefit from a diverse set of security controls, each contributing unique insights and capabilities. This collaborative approach enhances the organization's ability to detect and respond to cyber threats effectively. Moreover, zero trust provides a framework for continuous monitoring and adaptive security, allowing organizations to adapt to evolving threats and maintain a strong security posture over time.
If you want to learn more about how to fuse together risk signals and implement a zero trust architecture with a policy decision point, ZTS can help you.
ZTS is a consultancy dedicated to helping organisations plan, design and implement zero trust architectures.
Get in touch if you'd like to learn more about how to implement a Zero Trust Architecture for your enterprise.
