
Solve: Healthcare Multi-factor authentication (MFA)
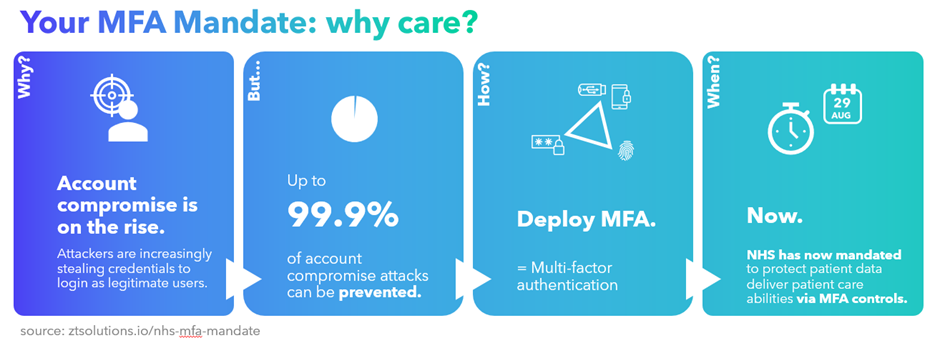
NHS has now mandated to protect patient data and deliver patient care services via MFA controls.
What should you do?
If you haven’t already, now is a good time to:
- Understand the NHS mandate / policy - you can find it here
- Check if you are prepared with the health check below.
- Analyse the best MFA options for your needs.
For your Service Users, Carers, Staff, and your wider workforce:
- Have you discovered and updated your data access flows?
-
- E.g. where does your admission data come from and go to?
- Do you have demographic data flowing from a trust to a hospital?
- Are they included in your Combined Information Assets and Flows Register (IAFR)?
-
- Is your organisation’s information asset register (IAR) up to date?
- For your IAFRs, have you secured the data collection process itself?
- Do you have an Identity Provider for authentication?
- Have you configured Single Sign On (SSO) where possible?
- Already have multiple MFA, define your strategy and reduce costs

How to protect your accounts
One of the greatest threats against your personal security is an attacker taking control of an online account. With it, a threat actor can do all sorts of nefarious deeds in your name, and if they get control of your email account, they can use password recovery features to control even more of your accounts. Fortunately, multi-factor authentication (MFA) can protect against account takeovers.


What is multi-factor authentication (MFA)?
You are probably likely familiar with the username and password authentication method. However, passwords have several problems. Humans aren’t the best at remembering passwords and are even worse at picking unique, complex passwords that can stand up to attacks. What’s more, people tend to reuse passwords, meaning that if one account is compromised, all the other accounts with the same password are also at risk.
Multi-factor authentication, sometimes known as two-factor authentication or 2FA, seeks to change that by using more than one authentication factor. That doesn’t mean a second password, but at least any two from a list of three possible factors:
- Something you know
- Something you have
- Something you are
Multi-factor authentication (MFA) is widely recognised as one of the most effective ways to protect data and accounts from unauthorised access. This policy will ensure that MFA is used on digital systems throughout the health sector, with particular requirements on accounts that are remotely accessible or have privileged access to systems.
Both the policy and guidance are aimed at senior IT leads, cyber security leads or any other appropriate person in organisations.
The policy has been adopted by the Department of Health and Social Care as guidance under s3(3)(b) of the Network and Information Systems (NIS) Regulations 2018. Organisations that are designated under the Regulations as operators of essential services for the health sector have a statutory obligation under s10(4) to have regard to such guidance.
This policy currently applies to:
- NHS trusts and foundation trusts
- integrated care boards
- arm’s length bodies of the Department of Health and Social Care
- commissioning support units in NHS England
- operators of essential services for the health sector in England as designated under the NIS Regulations
The accompanying guidance provides further details on how cyber, IT or the appropriate leads within your organisation can apply MFA within their own organisation and includes exemptions and scenarios to support implementation.

Something you know is typically a password. It lives in your head and is ideally known only to you. Something you have could be a USB security key or an authenticator app on your phone. It’s something that isn’t easy for a stranger to access or obtain. Finally, something you are is a physical characteristic that can be read with a biometric scan – such as a fingerprint scan or facial recognition.
Because it’s extremely unlikely an attacker will have more than one of these forms of authentication, MFA makes it much harder for threat actors to take over accounts. For example, when Google required their employees to use hardware MFA keys, account takeovers effectively vanished.
MFA has become a mainstay of the security industry over the past decade. The first generation of MFA commonly used a one-time authentication code sent over SMS. So, if you’ve ever had to input a one-time password (typically a series of six or eight numbers) then you’ve used MFA without knowing it.
The five most common multi-factor authentication methods
SMS-based one-time passwords (OTPs): where you log in with your username and password, and you're sent a 6 to 8-digit one-time password (OTP) that's different every time.
Hardware one-time password (OTP) tokens: hardware-based devices are usually in the form of a dongle on your keyring, smart card, or USB key. These devices generate one-time codes based on a cryptographic key stored inside the device.
Choosing the best multi-factor authentication for your Healthcare organisation
When shopping for a USB security key, you should look for FIDO U2F certification, which means it should work with most basic security key applications.
FIDO2/Web Authentication (WebAuthn) is the future-proof next-generation standard that can support additional types of authentication. If you want to use a device for biometric MFA or passwordless login, you’ll need FIDO2/WebAuthn.
Contact us by filling out the form below
Why ZTS?
We are a Zero Trust consultancy.
Our Zero Trust Solutions consultants can help you choose the right multi-factor authentication type for your business. We factor in many concerns, including:
- How the MFA will help with your passwordless and your Zero Trust journey
- Accessibility concerns across your organisation
- An end-to-end lifecycle process to account for loss, upgrades and stolen devices.